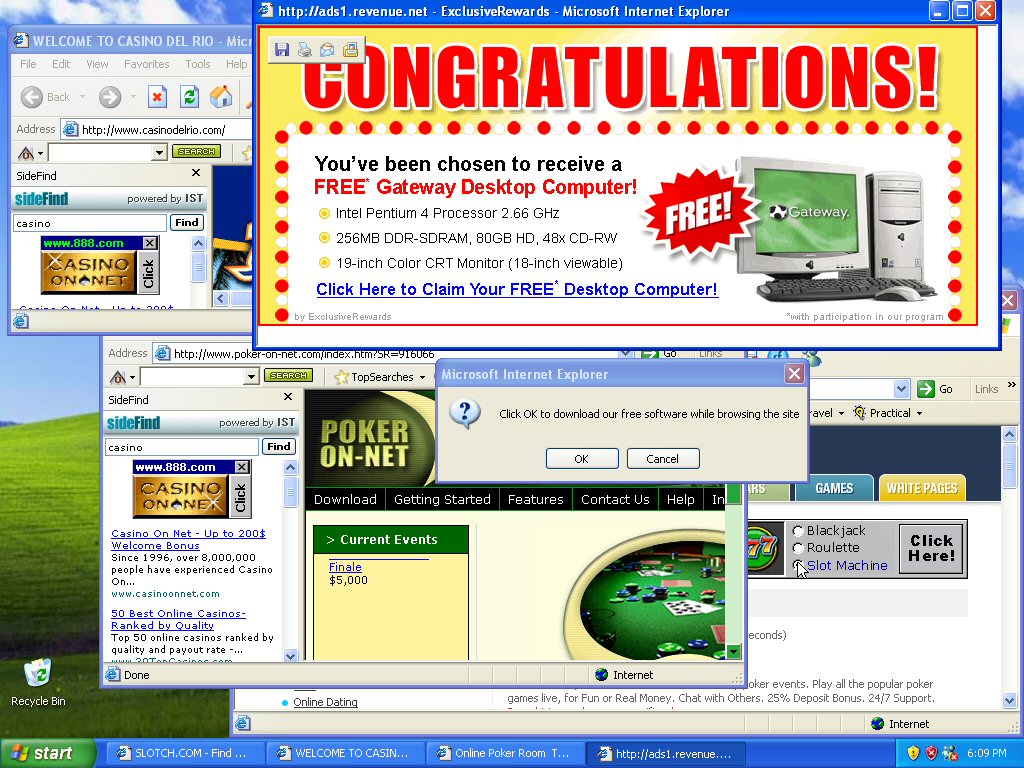
Did you know that your privacy can be breached by a simple ‘Yes’ or ‘No’ answer to popups on a web browser?
Yes, it can. When your privacy is breached, your security may be compromised.
And this is why you must always avoid answering ‘Yes’ or ‘No’ whenever those offers popup from your screen to your face. Instead of answering, it’s safer to just exit such popups by clicking on the “x” symbol usually at the top-right corner of the popup.
Whenever you answer ‘Yes’, ‘No’, or even click ‘Cancel’, a malware can be automatically installed as an extension on your browser. (Yes, even the ‘Cancel’ is no option at all!) Answering in any of these 3 ways may grant the malware rights to monitor your Internet behavior; control your access to a number of websites; and even make you visit unwanted advertisements sites or porn sites.
Also, the malware may save your passwords, credit-card details, personal information, or even work as a KeyLogger. A KeyLogger is an espionage tool with capacity to record and store every keystroke you make to a log file. That is a tool that can store everything you do on your computer; how you did them; the passwords you entered; and the sites you entered them in. With an advanced spyware as a KeyLogger or other spyware, the passwords collected are then sent to your predator in a remote location. The possible harms to you are better imagined.
Predators are always prying around, looking for the prey to catch. For instance, have you ever wondered how ATM Frauds are perpetuated? These predators do not always need your credit card to attack you. All that is needed is to gain access to your browser. As soon as this is done, all your details become theirs. Yes, just like that!
Before you freak out, there are certain precautions you can take. First, always read all information carefully before you accept anything. Second, always verify the developer company of any software or application before you install or use it. Third, whenever you do not feel comfortable with the level of access or permission requested, please do not hesitate to use an alternative software or application.
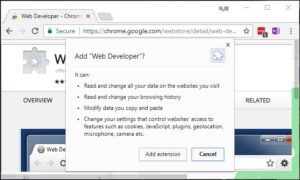
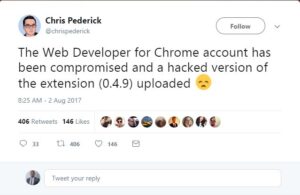
Also beware that though some browser extensions have good features and are without malicious intentions, these extensions may be hijacked by some good hacking techniques and thereafter used for various purposes. In August 2017, a popular extension, Web Developer, was reportedly hijacked and a malicious update was released. This affected many users. In today’s digital world, you must always be alert.
So it’s necessary to always take heed and look carefully before jumping on those awesomely featured, tiny-looking extensions.
Popups are not popcorns. Whenever you see them, be alert.