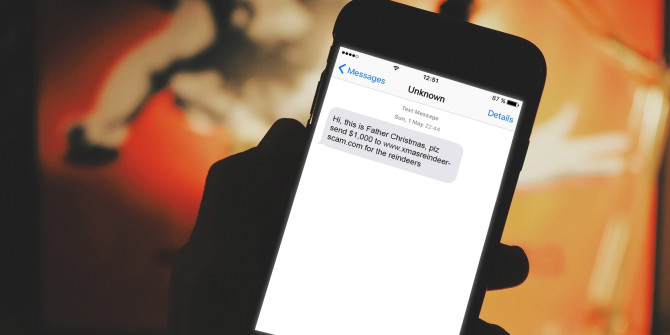
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 22. To view previous posts, click here. Cybercriminals seeking to break into your computer will use a type of malware known as a “Trojan Horse.” As this.. Read more

Day 22: Protect your computer and mobile devices from Trojan horses.
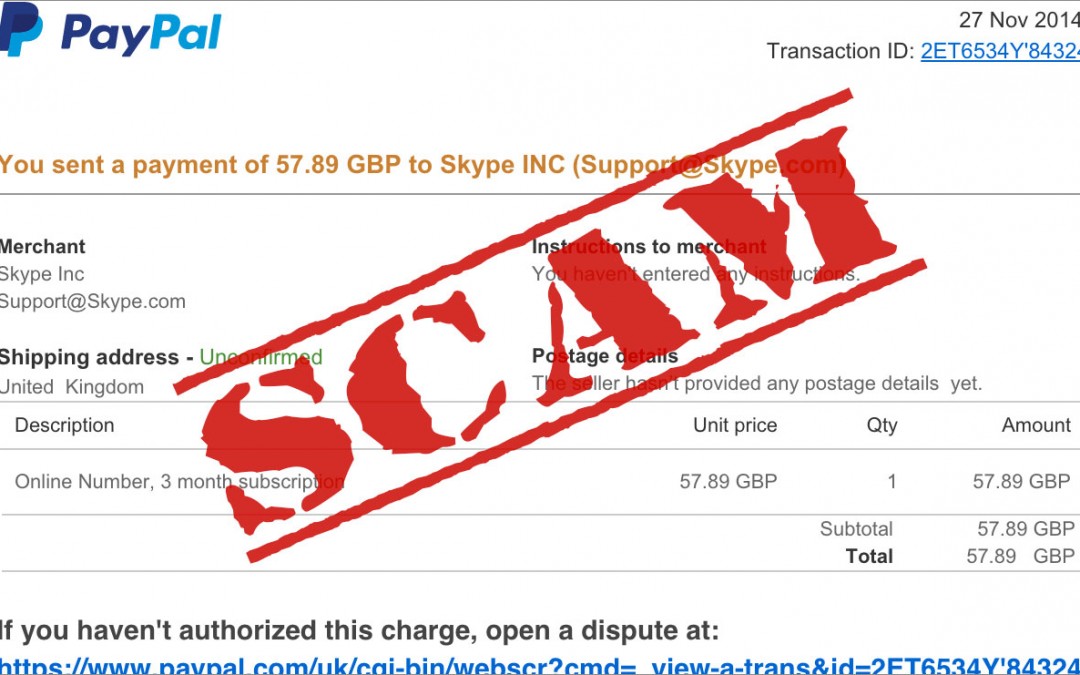
Day 21: Delete suspicious emails or contact the sender directly.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 21. To view previous posts, click here. Suspicious emails could be attempts to gather sensitive or confidential information. You need to be cautious about how you handle.. Read more

Day 20: Protect your home computer.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 20. To view previous posts, click here. To cybercriminals, an unprotected computer that’s always connected to the Internet can seem like an unlocked door. Malicious attackers can.. Read more

Day 18: Activate higher levels of protection on your browser.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 18. To view previous posts, click here. Cyberspace can be a dangerous place. There are many malicious applications and security vulnerabilities you could be exposed to online.. Read more
Day 17: Social Engineering: Never trust ANYONE with your personal information.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 17. To view previous posts, click here. Social engineering is the art of manipulating or tricking people into revealing personal or sensitive information such as bank details.. Read more

Day 15: Devote a single payment card for your online purchases to minimize risk.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 15. To view previous posts, click here. Devote a single payment card for your online purchases to minimize your risk. If you have more than one bank.. Read more

Day 16: When Online, ‘free’ isn’t always ‘free’.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 17. To view previous posts, click here. There are many free online services available on the Internet. From storing of documents or media in the cloud to.. Read more

Day 13: Use only trusted app stores such as the Apple App Store and Google Play.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 13. To view previous posts, click here. Malicious programs or malware often infect a mobile device when you download applications from an untrusted source. This is one.. Read more