Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 26. To view previous posts, click here. Certain types of attachment are more dangerous than others. While viruses and malware can potentially be embedded in most types.. Read more

Day 26: Never open .exe files from your email.

Day 24: Beware of SEO poisoning whenever you use a search engine.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 24. To view previous posts, click here. Cybercriminals use search engine optimization (SEO) to trick you into visiting malware sites. SEO poisoning is an attack method that.. Read more

Day 23: Rooting your phone or device can be dangerous.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 23. To view previous posts, click here. Rooting is a process that allows a user to have superuser rights. With superuser right, you have privileges to modify.. Read more

Day 22: Protect your computer and mobile devices from Trojan horses.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 22. To view previous posts, click here. Cybercriminals seeking to break into your computer will use a type of malware known as a “Trojan Horse.” As this.. Read more
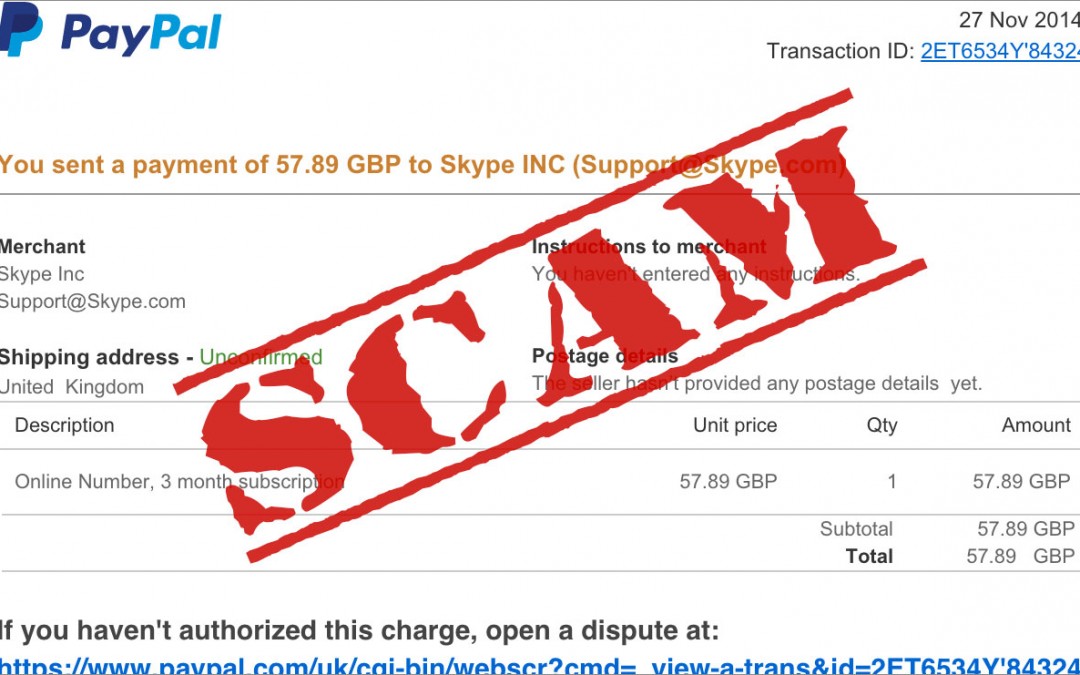
Day 21: Delete suspicious emails or contact the sender directly.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 21. To view previous posts, click here. Suspicious emails could be attempts to gather sensitive or confidential information. You need to be cautious about how you handle.. Read more

Day 13: Use only trusted app stores such as the Apple App Store and Google Play.
Welcome to Cybersecurity in 31 Days. I’m Malan Faya, your host. Today is Day 13. To view previous posts, click here. Malicious programs or malware often infect a mobile device when you download applications from an untrusted source. This is one.. Read more
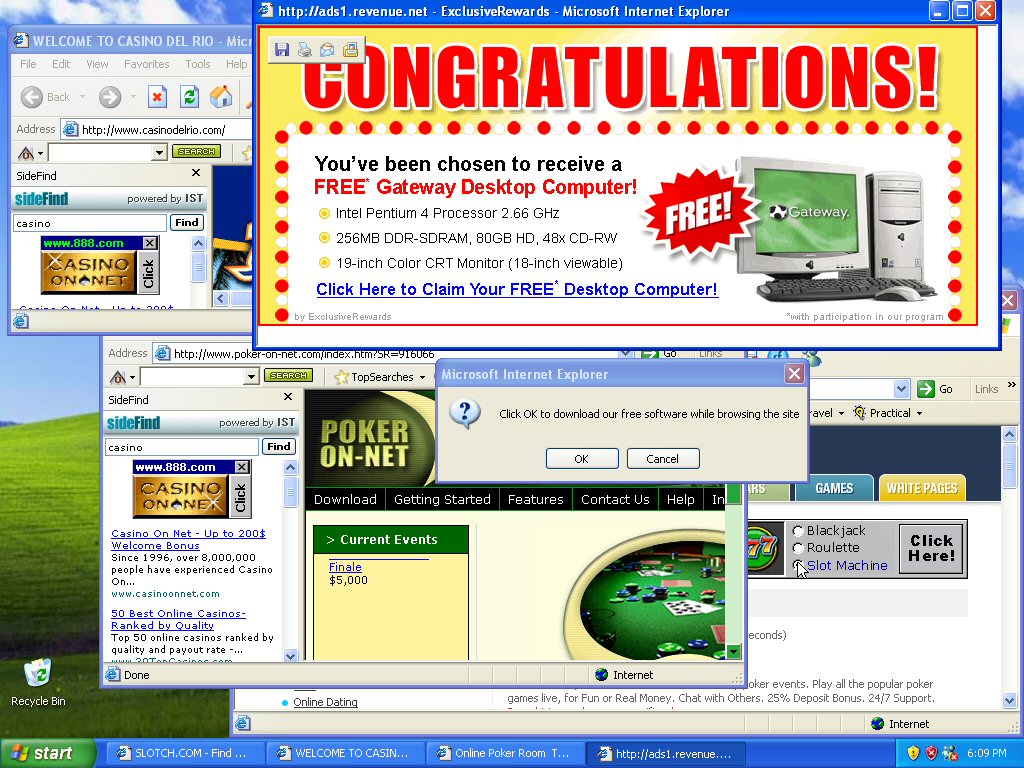
Popups: How Clicking ‘YES’ or ‘No’ Can Compromise Your Security
by Mallick Bolakale Did you know that your privacy can be breached by a simple ‘Yes’ or ‘No’ answer to popups on a web browser? Yes, it can. When your privacy is breached, your security may be compromised. And this is.. Read more


